Enable sensitivity labels on Azure AD
1. Open a Windows PowerShell window on your computer. You can open it without elevated privileges.
2. Run the following commands to prepare to run the cmdlets.
Install-Module AzureADPreview Import-Module AzureADPreview AzureADPreview\Connect-AzureAD
On the Sign in to your account page, enter your admin account and password to connect you to your service, and select Sign in.
3. Fetch the current group settings for the Azure AD organization and display the current group settings.
$grpUnifiedSetting = (Get-AzureADDirectorySetting | where -Property DisplayName -Value "Group.Unified" -EQ) $Setting = $grpUnifiedSetting $grpUnifiedSetting.Values
4. Enable the feature:
$Setting["EnableMIPLabels"] = "True"
A Microsoft documentation is available here for more details.
Synchronize your sensitivity labels to Azure AD and activate it for containers
1. To synchronize your sensitivity labels to Azure AD, you need first to connect to Security & Compliance PowerShell.
For example, in a PowerShell session that you run as an administrator, sign in with a global administrator account.
2. Then run the following command to ensure your sensitivity labels can be used with Microsoft 365 groups:
Execute-AzureAdLabelSync
3. You can now enable sensitivity labels on groups and sites here while creating or editing a label in Microsoft Purview Information.
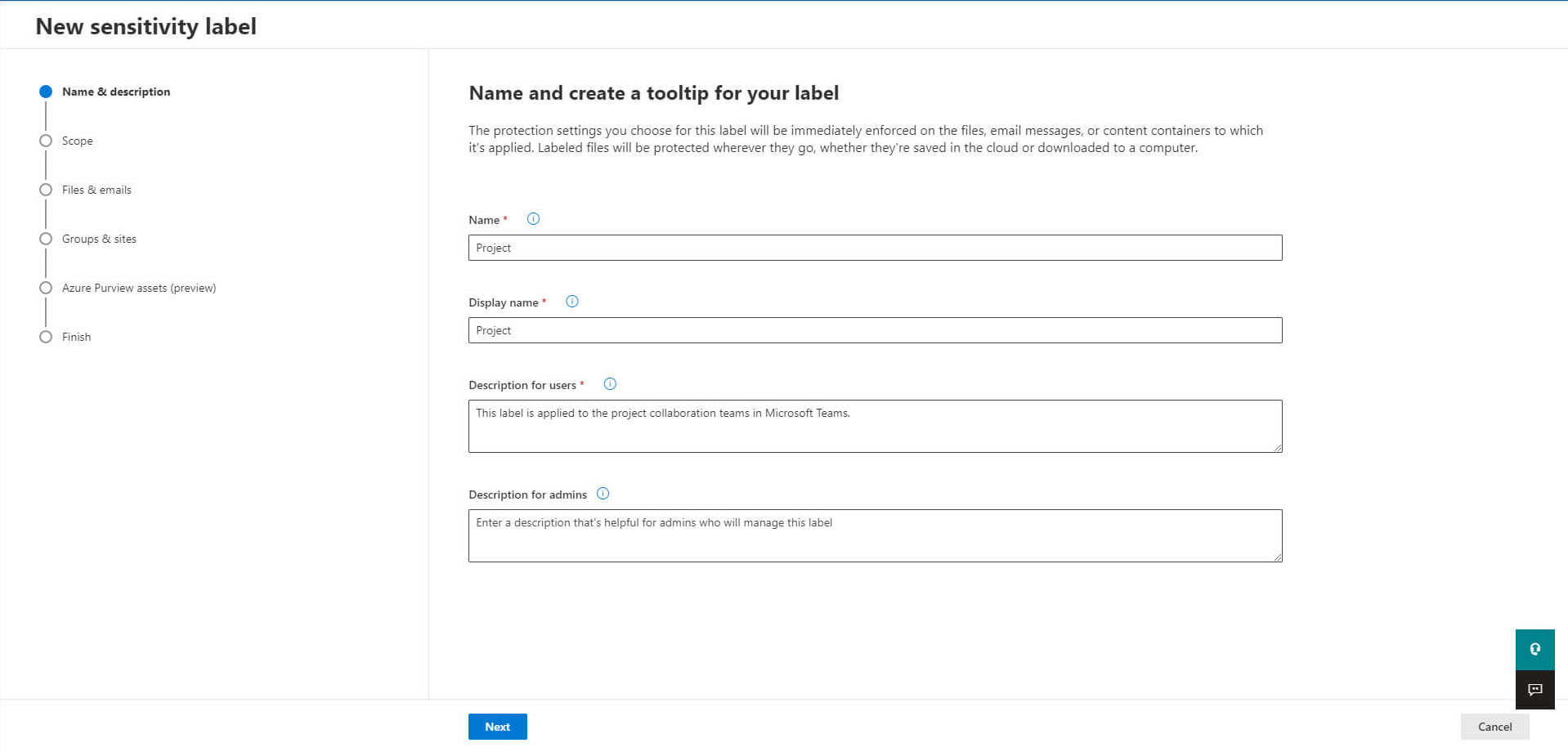
Create a sensitivity label
Now that all the prerequisites have been checked, you can create a new sensitivity label in Microsoft Purview Information.
Provide a name and description to your label:
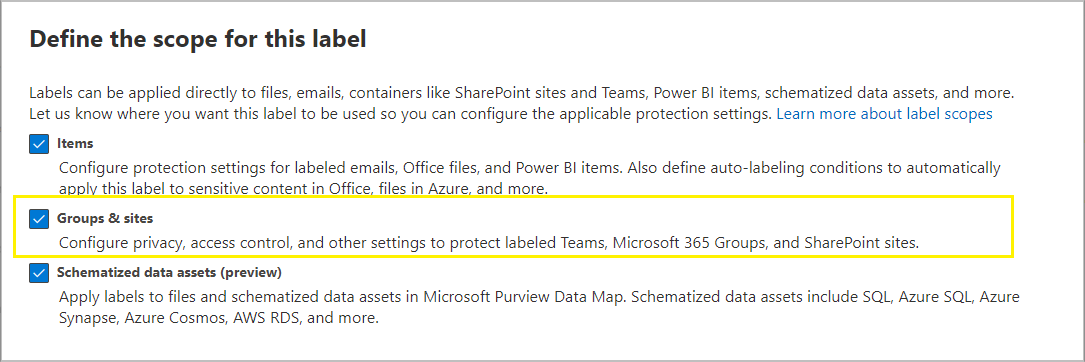
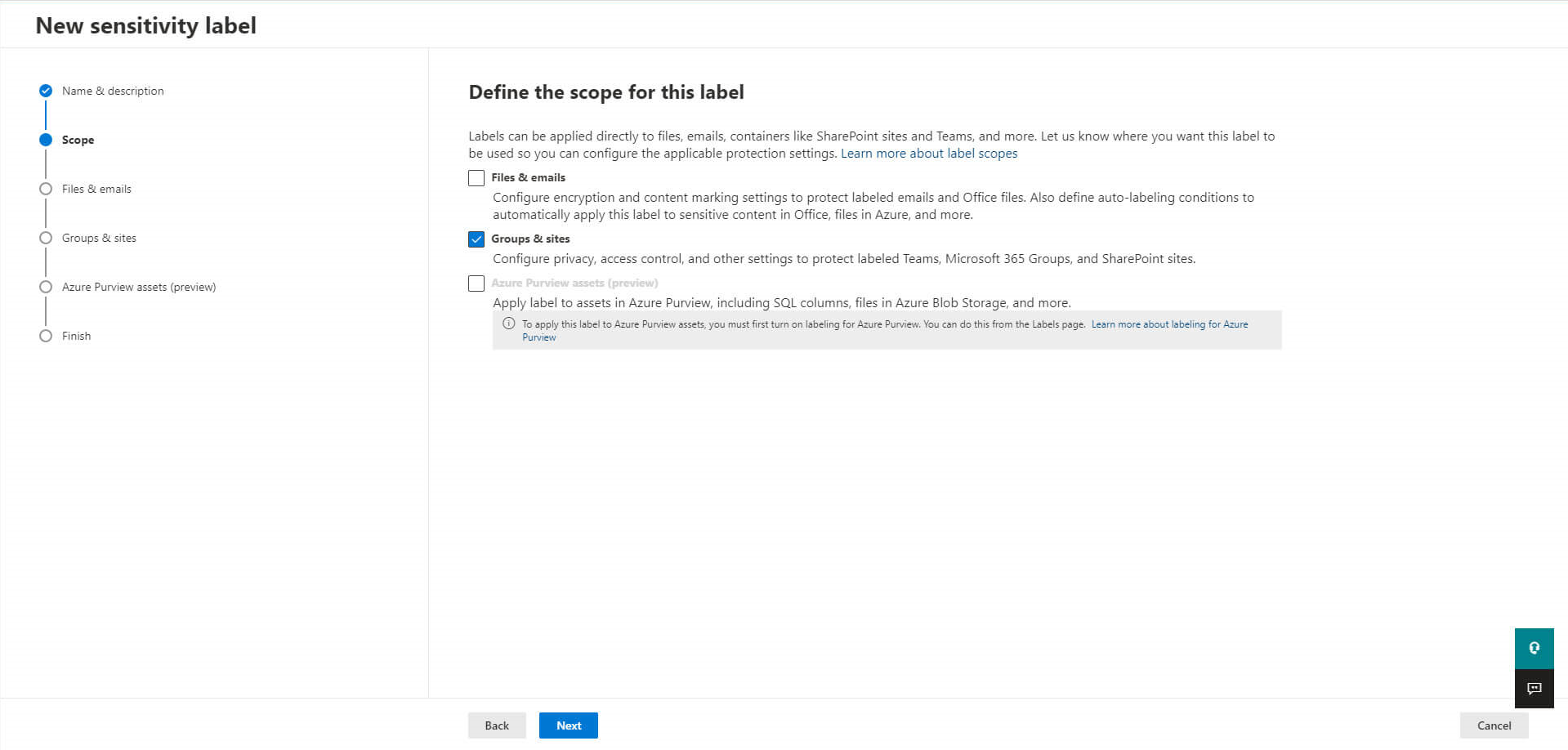
Define the scope of your label to let it be applied to groups and sites:
Configure your protection settings:
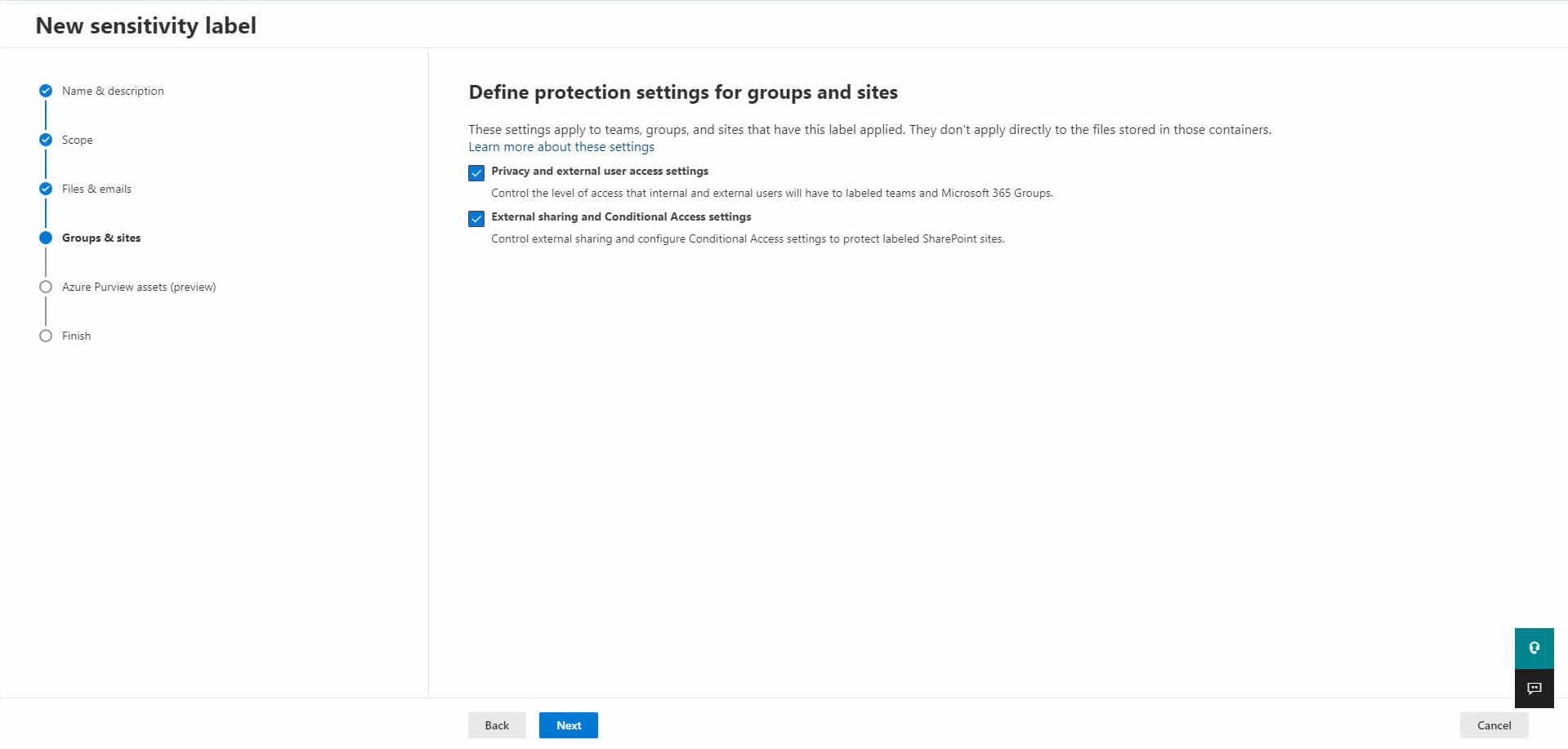
First with external user access settings:
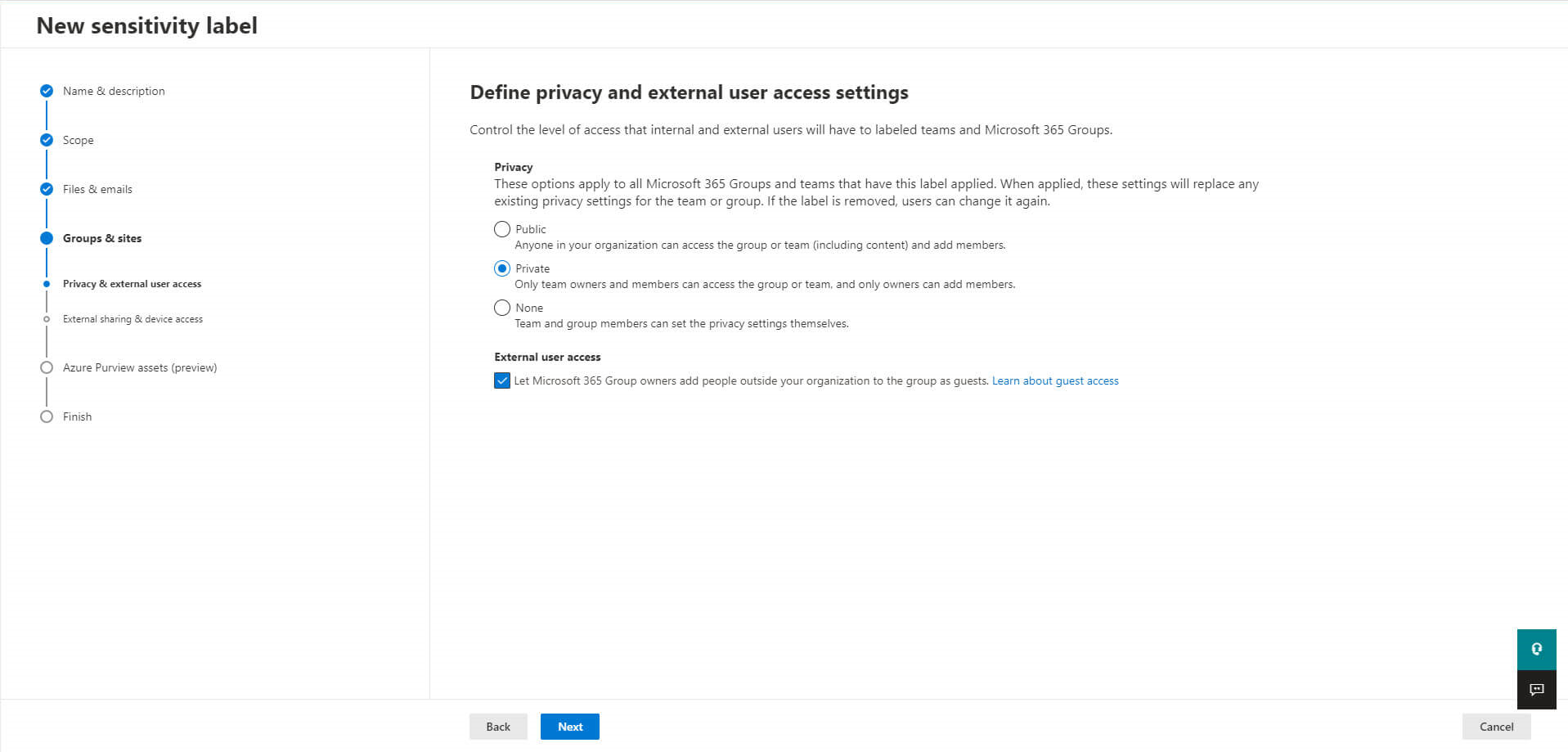
And then with external sharing and device access:
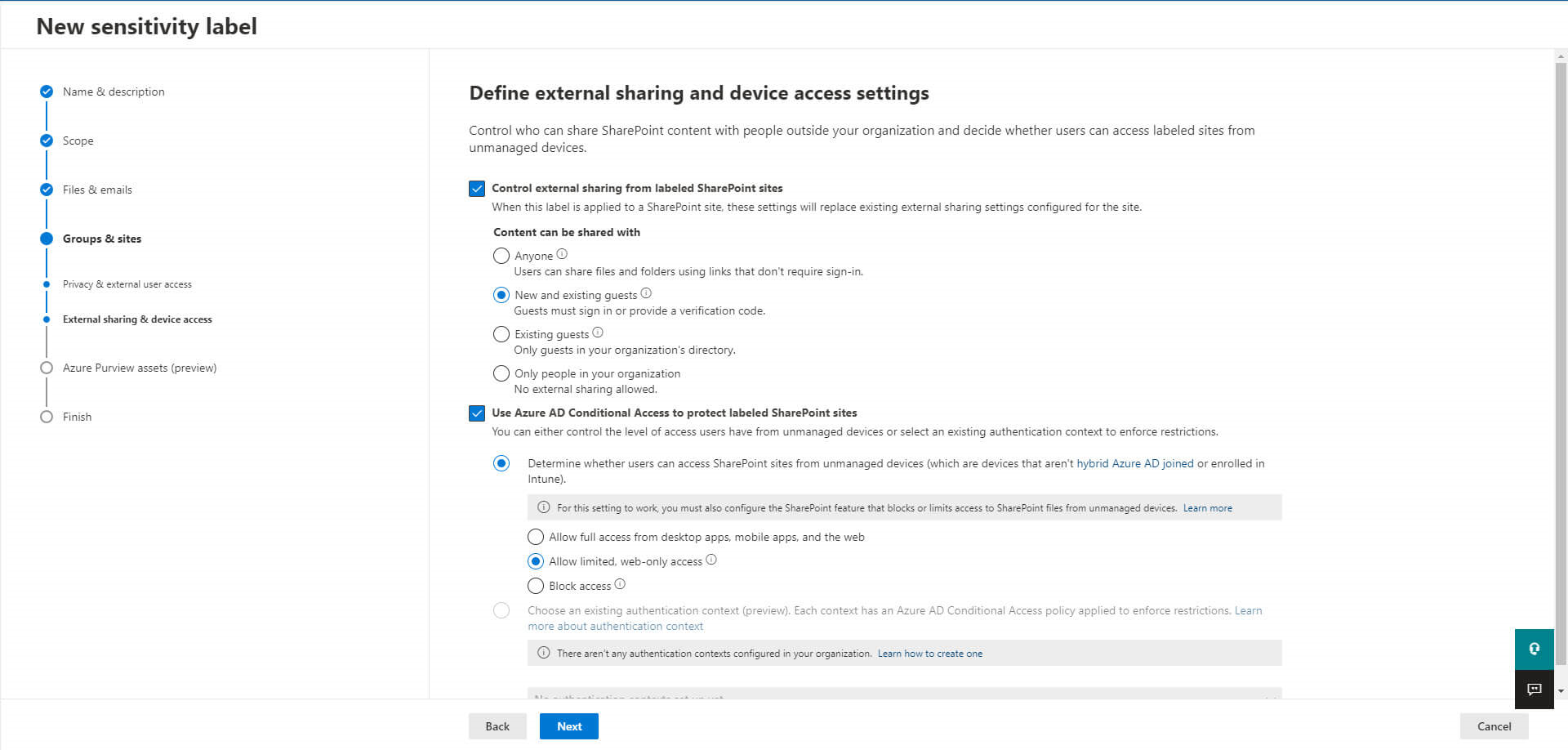
The last step is now to publish this new label:
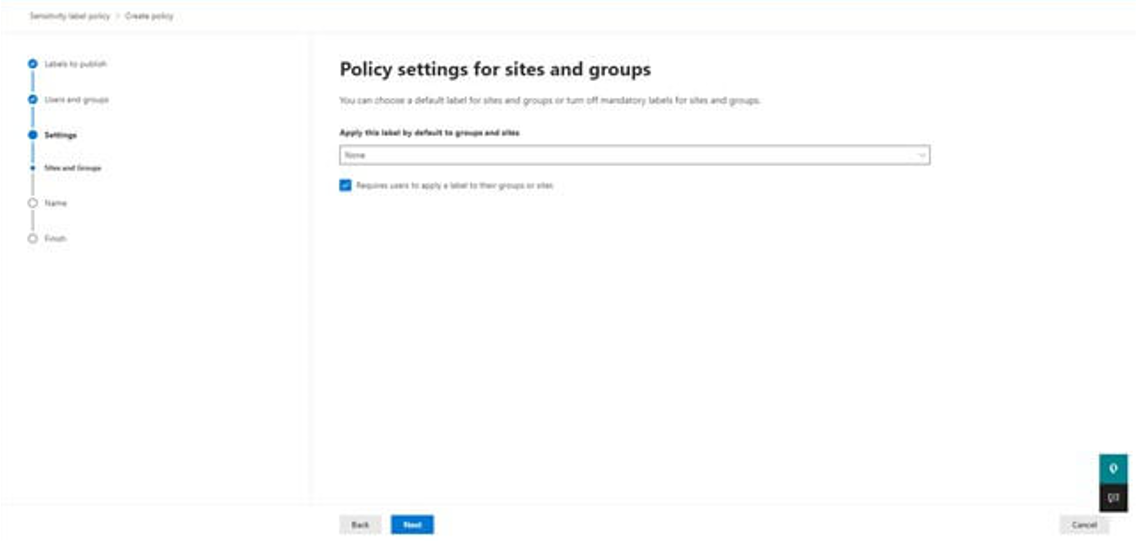
Here you can select the default label you want to apply while creating a new team:
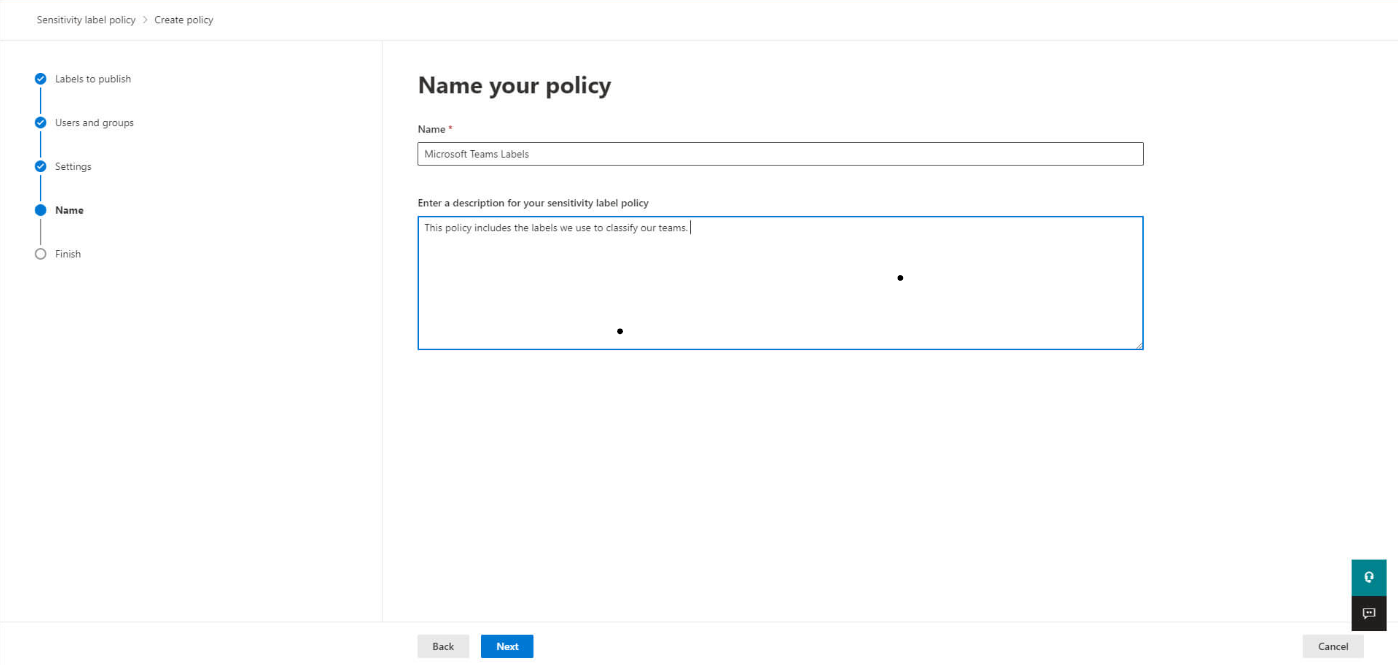
And finally name your policy:
What about team classification?
Team’s classification labels are text strings you associate with a Microsoft 365 group, but they do not have any associated controls or policies.
The team’s classification labels are simply metadata; for security, you will need to use Sensitivity labels and policies. The classification labels need adding using PowerShell, and you cannot combine them with Sensitivity labels.
Want to know more about improving your Microsoft Teams experience?
Powell Teams helps IT and end-users overcome common Microsoft Teams problems while at the same time providing an improved and engaging collaborative experience. Discover more about how to take your Microsoft Teams collaboration experience to the next level for both IT teams and users with Powell Teams.